
Quantum Cryptography
Securing the Unbreakable?
In our increasingly interconnected digital world, the security of information is paramount. From sensitive government communications to everyday online transactions, we rely on cryptography to protect our data from prying eyes. However, the advent of powerful quantum computers poses a potential threat to many of the classical encryption methods we use today. Enter quantum cryptography, a revolutionary approach to security that leverages the fundamental laws of quantum mechanics to offer a promise of virtually unbreakable communication.
Key Concepts in Quantum Cryptography
The Quantum Advantage for Security
Quantum cryptography relies on several key quantum mechanical principles to achieve its enhanced security:
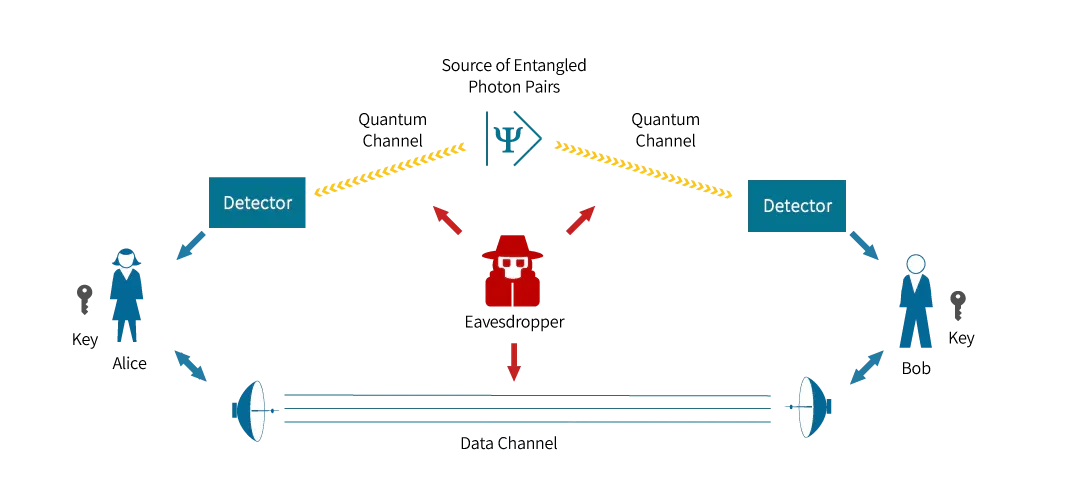
- Quantum Key Distribution (QKD): This is the most well-known application of quantum cryptography. QKD allows two parties to establish a shared secret key by transmitting information encoded in quantum states, such as the polarization of individual photons. This key can then be used to encrypt and decrypt messages using classical encryption algorithms.
Charles Bennett and Gilles Brassard: In 1984, they developed the BB84 protocol, one of the first and most well-known quantum key distribution protocols, laying the foundation for practical quantum cryptography.
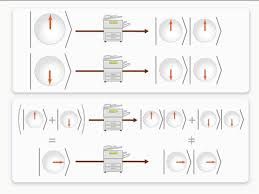
- No-Cloning Theorem: A fundamental principle of quantum mechanics states that it is impossible to create an identical copy of an arbitrary unknown quantum state. This is crucial for QKD because it means that any attempt by an eavesdropper to intercept and copy the quantum information carrying the key will inevitably leave a trace
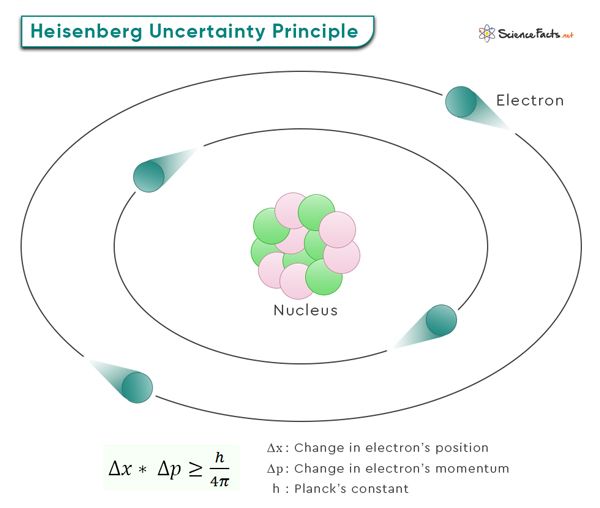
- Heisenberg Uncertainty Principle: This principle dictates that certain pairs of physical properties, such as the position and momentum of a particle, cannot be known with perfect accuracy simultaneously. In the context of QKD, this means that any attempt to measure the quantum state of the photons to gain information about the key will inevitably disturb those states, making the eavesdropping detectable by the legitimate communicating parties.
How Quantum Key Distribution (QKD) Works
A Step-by-Step Look
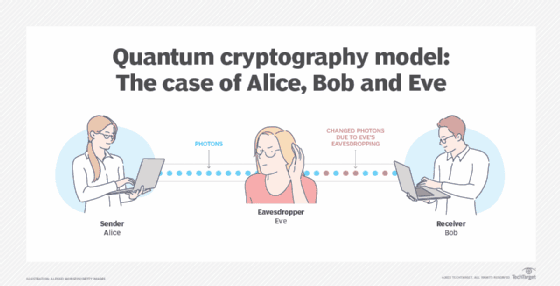
Let's take a simplified look at how Quantum Key Distribution (QKD) typically works, using a common protocol like BB84:
- Quantum Transmission: Alice (the sender) wants to send a secret key to Bob (the receiver). She generates a random sequence of bits (0s and 1s) and encodes each bit onto a photon by choosing a random polarization basis (e.g., rectilinear: horizontal/vertical, or diagonal: +45°/-45°). For example, a horizontal polarization might represent a '0' in the rectilinear basis, and a +45° polarization might represent a '1' in the diagonal basis. Alice then sends these polarized photons to Bob through a quantum channel (typically a fiber optic cable or free space).
- Quantum Measurement: Bob receives the photons and measures the polarization of each one. Crucially, Bob also randomly chooses a measurement basis (either rectilinear or diagonal) for each incoming photon, independently of Alice's choice.
- Classical Communication: After Bob has measured all the photons, Alice and Bob communicate over a classical, public channel (like the internet). They compare the basis they used for each photon. For all the photons where they used the same basis, their measurements should ideally correlate (e.g., if Alice sent a horizontally polarized photon and Bob measured in the rectilinear basis, he should also get horizontal).
- Key Sifting: Alice and Bob discard the bits where they used different bases. The remaining bits, for which they used the same basis, form a shared raw key.
- Error Detection: To check for eavesdropping, Alice and Bob publicly compare a small, random subset of their raw key bits. If an eavesdropper (Eve) has tried to intercept the photons, her measurements would have inevitably disturbed the polarization states (due to the no-cloning theorem and the uncertainty principle), leading to a higher error rate in the compared bits than what would be expected from normal transmission noise. If the error rate exceeds a certain threshold, they know an eavesdropper is present and might discard the key and try again.
- Privacy Amplification: If the error rate is acceptable, Alice and Bob apply a process called privacy amplification to further reduce the possibility of Eve having any significant information about the key. The resulting final key is a secret and secure key that can be used for classical encryption.
Beyond Key Distribution
Other Quantum Cryptographic Techniques
While QKD is the most prominent application, quantum mechanics offers other avenues for enhancing security:
- Quantum Random Number Generation (QRNG): True randomness is essential for strong cryptography. Classical computers rely on algorithms to generate pseudo-random numbers, which can be predictable. QRNG leverages inherently random quantum processes, such as the probabilistic outcome of measuring a quantum state, to generate truly unpredictable random numbers for cryptographic applications.
- Quantum Secure Direct Communication (QSDC): This technique aims to directly transmit the secret message itself encoded in quantum states, rather than just a key. While still an active area of research, QSDC holds the potential for highly secure communication without the need for a separate key exchange in some scenarios.
- Post-Quantum Cryptography (PQC): Recognizing the future threat of quantum computers breaking current public-key encryption algorithms (like RSA and ECC), researchers are developing classical cryptographic algorithms that are believed to be resilient to attacks from both classical and quantum computers. These algorithms, often based on mathematical problems different from those vulnerable to Shor's algorithm, are crucial for ensuring long-term security in the quantum era.
Applications of Quantum Cryptography
Protecting Sensitive Information
The unique security properties of quantum cryptography make it ideal for protecting highly sensitive information across various sectors:
- Government and Military: Securing classified communications and protecting national secrets.
Organizations and governments around the world are beginning to implement QKD for securing highly sensitive communication links, demonstrating its growing practical relevance.
- Financial Institutions: Ensuring the security of banking transactions and protecting sensitive financial data.
- Healthcare: Protecting patient privacy and the security of medical records.
- Critical Infrastructure: Safeguarding essential services like power grids, water treatment facilities, and telecommunications networks from cyberattacks.
- Data Centers: Securing the vast amounts of data stored and transmitted by data centers.
Challenges and the Future of Quantum Cryptography
Navigating the Quantum Landscape
Despite its promise, quantum cryptography faces several challenges:
- Distance Limitations: Current QKD systems using fiber optic cables are limited by photon loss over long distances. While advancements are being made, achieving truly global secure communication often requires trusted relays or satellite-based QKD.
- Cost and Complexity: Implementing and maintaining quantum cryptographic systems can be expensive and complex compared to traditional methods.
- Practical Vulnerabilities: While theoretically unbreakable, real-world implementations of QKD can have vulnerabilities in the hardware and software used.
- The Quantum Threat to Current Cryptography: The development of large-scale, fault-tolerant quantum computers could potentially break many of the public-key encryption algorithms currently used to secure the internet. This necessitates the development and adoption of post-quantum cryptography.
Shor's Algorithm, a quantum algorithm discovered in 1994, has the potential to efficiently factor large numbers, which is the mathematical basis for the security of widely used public-key encryption methods like RSA.
The future of quantum cryptography is likely to involve a combination of approaches, including advancements in QKD technology (longer distances, lower costs), the development and standardization of robust post-quantum cryptography algorithms, and the integration of both quantum and classical security measures to create layered defense strategies. Satellite-based QKD holds significant promise for enabling secure communication over global distances.
Quantum Cryptography in India
Securing the Nation's Digital Future
India recognizes the critical importance of quantum cryptography for national security and is actively investing in research and development in this field as part of the National Quantum Mission (NQM). Initiatives are underway to develop and test Quantum Key Distribution (QKD) systems for secure communication between government facilities and critical infrastructure. Indian research institutions and startups are also working on advancing quantum-safe cryptography algorithms and exploring various applications of quantum cryptography to secure the nation's digital future.
Learn more about the National Quantum Mission (NQM) on the Department of Science & Technology website.
Explore the Quantum Realm Further
Delving Deeper into Secure Communication
The field of quantum cryptography is rapidly evolving, offering exciting possibilities for the future of secure communication. To learn more about this fascinating area, we encourage you to explore the following resources:
- The US National Institute of Standards and Technology (NIST) leads the effort to standardize quantum-resistant cryptography. Their project page is a central resource.
- The Institute for Quantum Computing (IQC) at the University of Waterloo is a world-leading center with strong research across quantum information, including cryptography.
- Follow industry developments and news coverage - The Quantum Insider (Search for Cryptography/Security)